Microsoft Security Space
Welcome to our Microsoft Security Space. Here you will find all you need
to know about Microsoft Security and how you can help your clients.
.jpg?width=3000&height=1320&name=sec%201%20(1).jpg)
As we know your clients big and small face huge challenges when it comes to cyber threats and their own security.
A shift to cloud computing which most of your clients have done (with some late bloomers following suit) has inadvertently shifted their perimeters. Our Firewall used to be the permitter. Our cloud services do not live behind this, rather they are accessed with two simple pieces of information. A username & a password, your best friends, and you worst enemies in one.
Add to this, the challenge we now see with ubiquitous access to smart devices. These are not just phones, they are small powerful computers, that connect to the internet always. They also, have apps that are connect to your Cloud services; hence these devices have your data on them.
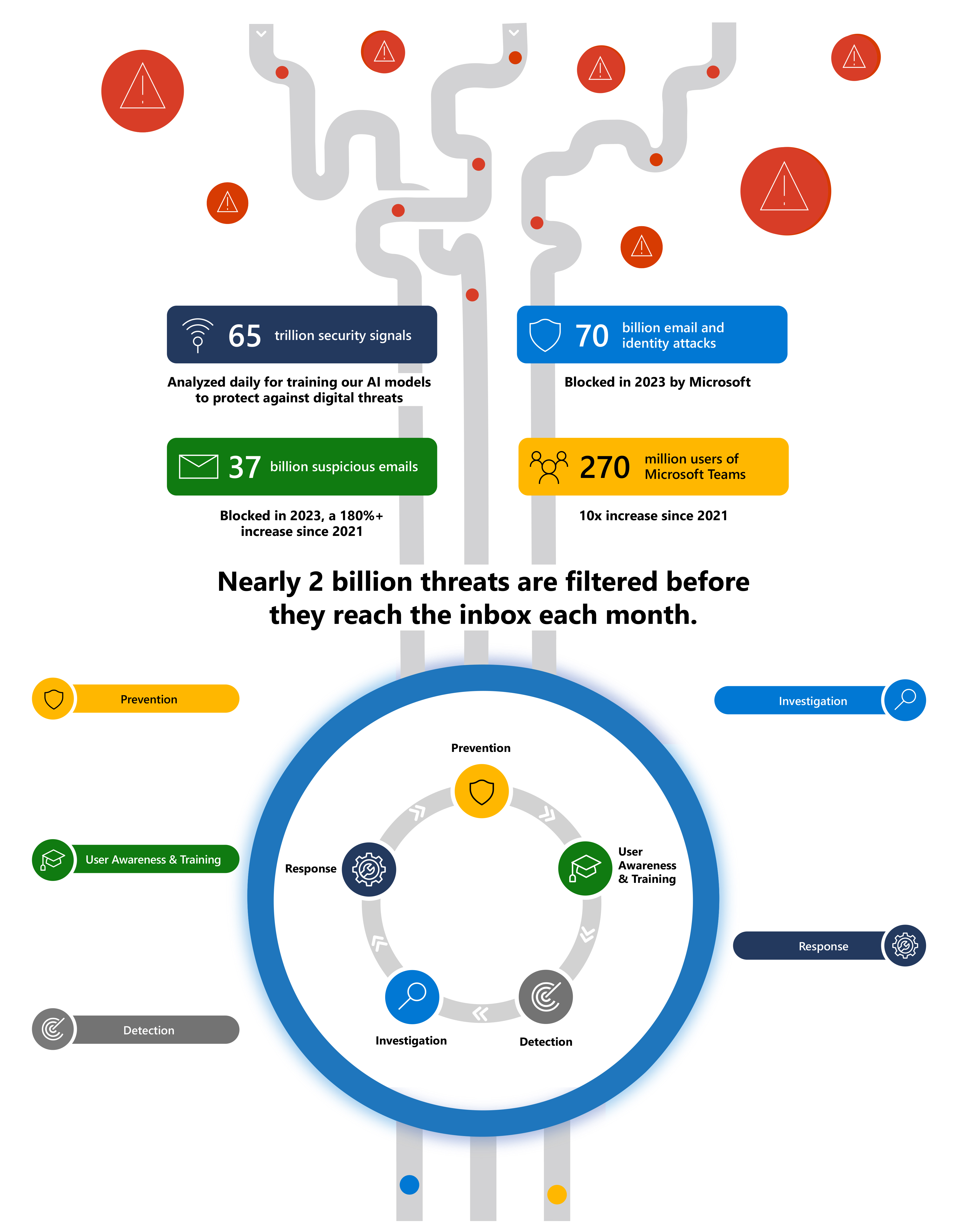
Managing your devices is a challenge every SME in Ireland has, without exception. Always knowing what is connecting to your data is a key imperative, that we can help with. This is further compounded by data protection laws that apply to businesses of all sizes in our country like GDPR and your payroll data which would be classified as PCI related data. In 2023 the European union are extending the reach of NIST 2.0 and including even more verticals that will impact of your clients. Even for those who do not legally fall into this category they need to derive and practice their own security standards. This is where you as the MSP comes in to help them make sense of it all.
Microsoft 365’s Security Fabric
The term fabric is one that our team love, as it conjures a simple image of a blanket that covers everything. It is that very principle of covering everything that we must try to help our clients understand.
The Microsoft 365 Business Premium/E3 and E5 SKUS offer unparalleled security services that address the following security focus areas and allow MSP's to build profitable service offerings
Identity and Access Management | Your New/extended perimeter:
Staring with business premium we see the introduction of Azure AD P1 which makes the basic version of Azure AD very useful. Partners can now work with clients to ensure Identity and access management is centralised.
Azure AD integrate with over 4,500 SaaS applications and will also integrate with the majority of Firewall vendors to secure on premise access too. Giving partners and their clients a centralised identity and access management portal.
Unified Endpoint Management:
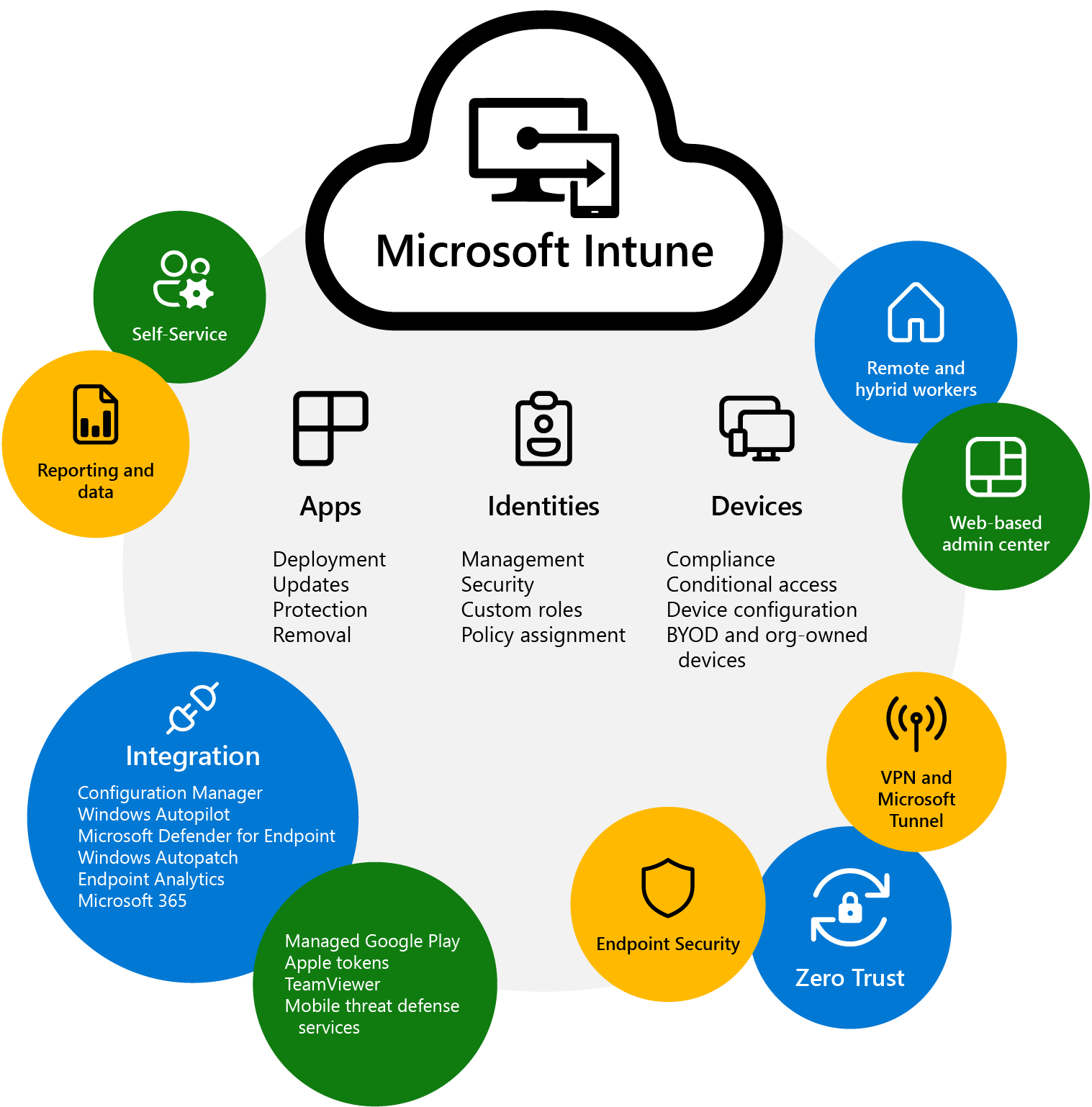
Intune is included in all M365 bundles from Business Premium to E5. This clever tool allows MSPs and their clients take control back across their now diverse device estates. Regardless of operating system, you can manage devices, or applications that contain business data.
Start to contemplate BYOD scenarios to reduce capital expenditure on hardware, re-imagine the management and delivery of your end users devices.
Data Compliance and Data Protection:
Compliance manager and Azure Information protection make their appearance as low down as M 365 BP and all the way up to M365 E5 with plenty of tools at your disposal. Some features are advanced features and require clients to adopt E5. But as a starting point, clients and MSPs can start to look at data classification templates and start to understand how they can take control of their data. Partners can configure DLP polices targeting Office365 services and your devices/apps.
If your client wants granular document level tagging of data, partners can deploy AIP across the environment. With Intune and Windows 10 for business, information protection tools can be enabled on Windows devices along side encryption of laptops by default. SME’s and partners have never had these level of technology before, and it offers huge value when deployed.
Learn more about compliance here:

Deployment Guidance:
Our Technical team often get contacted by our partners when deployments are due to be tackled. We often have partners asking us for guidance and advice on how to deploy security controls. It is always a difficult question to answer as each clients site will differ.
Through our framework we help partners "Build" offers that introduce standards in terms of security. To help with this we have drafted an E-Book on how to deliver Zero Trust deployments helping partners to identify what services need to be enabled.
To go a step further we have also created training paths based on the advice in this E-Book. Partners can download the E book here and also book into our practical Zero Trust Deployment Learn Lab.
Request ebooks
Advanced Security Services with Defender for 365 & Endpoint:
Microsoft Defender for 365 and Defender for Endpoint Services provide comprehensive and integrated security solutions that help organizations protect their digital assets, detect threats in real-time, respond effectively to incidents, and enhance their overall cybersecurity posture.
Comprehensive Threat Protection: Both Microsoft Defender for 365 and Defender for Endpoint Services provide robust protection against various types of threats, including malware, viruses, ransomware, phishing attacks, and advanced persistent threats (APTs). They utilize advanced machine learning and behavior-based analytics to detect and block emerging and sophisticated threats.
Endpoint Detection and Response (EDR):>Defender for Endpoint Services offers powerful EDR capabilities, enabling organizations to proactively detect and respond to security incidents on endpoints. It provides real-time monitoring, threat hunting, and investigation tools, allowing security teams to quickly identify and mitigate potential breaches.
Cloud-Based Protection: Both services leverage the power of the cloud to provide scalable and efficient threat protection. They utilize Microsoft's extensive threat intelligence network and cloud infrastructure to rapidly identify and respond to emerging threats, ensuring that organizations stay protected against the latest attack vectors.
These services seamlessly integrate with other Microsoft products and services, such as Microsoft 365, Azure, and Windows, creating a cohesive security environment. This integration allows for improved visibility, control, and response to threats across the entire ecosystem, enhancing overall security posture.